目录
实验模拟两个企业内网跨网段通讯,通过VPN隧道技术实现加密跨外网通信
一.实现全网互通
1.配置ip(遵循上一下二原则)
2.配置静态路由(因为路由拓扑比较简单所以不用使用动态路由协议)
二.配置acl实现源地址转换,达到内网设备可以访问外网的效果
三.配置IPsec
四.NAT豁免
实验模拟两个企业内网跨网段通讯,通过VPN隧道技术实现加密跨外网通信
下面为拓扑图
实验环境请看数通路由协议实验
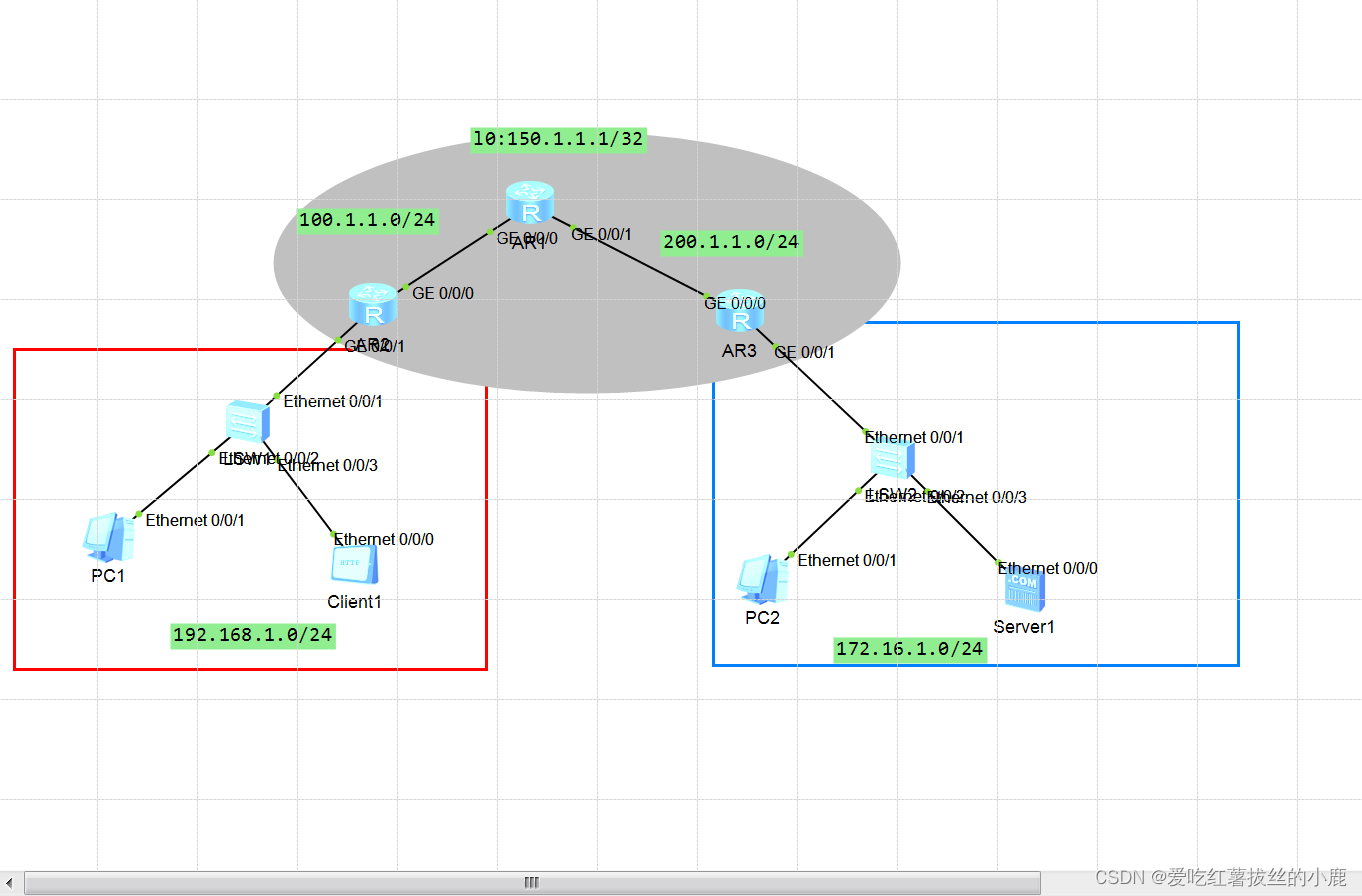
注:左面区域为192.168.1.0网段,北京总公司
右边区域为172.16.1.0网段,上海分公司
AR2,AR3模拟两个内网区域网段的边缘设备,也就是网关,灰色区域模拟互联网
下面是配置过程(AR2即R2)
一.实现全网互通
1.配置ip(遵循上一下二原则)
<R2>sys
[R2]int g0/0/0
[R2-GigabitEthernet0/0/0]ip add 100.1.1.2 24
<R3>sys
[R3]int g0/0/0
[R3-GigabitEthernet0/0/0]ip add 200.1.1.2 24
<R1>sys
[R1]int l0
[R1-LoopBack0]ip add 150.1.1.1 32
[R1-LoopBack0]int g0/0/0
[R1-GigabitEthernet0/0/0]ip add 100.1.1.1 24
[R1-GigabitEthernet0/0/0]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 200.1.1.1 24
2.配置静态路由(因为路由拓扑比较简单所以不用使用动态路由协议)
[R2]ip route-static 0.0.0.0 0.0.0.0 100.1.1.1
[R3]ip route-static 0.0.0.0 0.0.0.0 200.1.1.1
左右R2,R3分别配置静态路由,这里的0.0.0.0 0.0.0.0 100.1.1.1 ,意思就是不管是要去哪个ip地址都转发到100.1.1.1

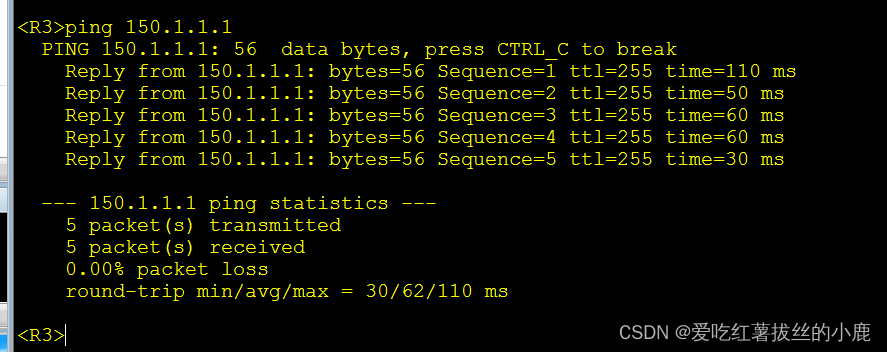
二.配置acl实现源地址转换,达到内网设备可以访问外网的效果
记住这里的acl 3000,后面还有一个acl 3001,注意区别
[AR2]acl 3000
[AR2-acl-adv-3000]rule permit ip source 192.168.1.0 0.0.0.255
[AR2-acl-adv-3000]di th
[V200R003C00]
#
acl number 3000
rule 5 permit ip source 192.168.1.0 0.0.0.255
#
return
[AR2-acl-adv-3000]q
[AR2]int g0/0/0
[AR2-GigabitEthernet0/0/0]nat outbound 3000
[AR2-GigabitEthernet0/0/0]di th
[V200R003C00]
#
interface GigabitEthernet0/0/0
ip address 100.1.1.2 255.255.255.0
nat outbound 3000
#
return
[AR2-GigabitEthernet0/0/0]q
[AR3]ip route-static 0.0.0.0 0.0.0.0 200.1.1.1
[AR3]acl 3000
[AR3-acl-adv-3000]rule permit ip source 172.16.1.0 0.0.0.255
[AR3-acl-adv-3000]di th
[V200R003C00]
#
acl number 3000
rule 5 permit ip source 172.16.1.0 0.0.0.255
#
return
[AR3-acl-adv-3000]q
[AR3]int g0/0/0
[AR3-GigabitEthernet0/0/0]nat outbound 3000
[AR3-GigabitEthernet0/0/0]di th
[V200R003C00]
#
interface GigabitEthernet0/0/0
ip address 200.1.1.2 255.255.255.0
nat outbound 3000
#
return
[AR3-GigabitEthernet0/0/0]q
[AR3]
这里有个细节,也就是边缘路由器需要在内侧配置网关,这里重点就是内侧,也就是边缘路由器的内网接口,而acl要配到外侧(靠近目的地的一端)
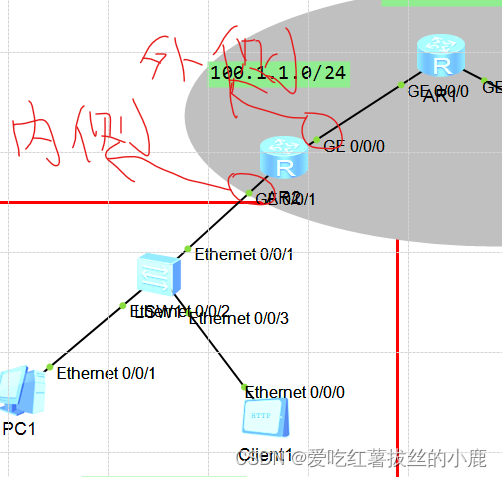
外侧配acl,内侧配网关(重点)
[R2]int g0/0/1
[R2-GigabitEthernet0/0/1]ip add 192.168.1.254 24
[R3]int g0/0/1
[R3-GigabitEthernet0/0/1]ip add 172.16.1.254 24
这里还有一个细节也就是内网设备的网关要配置的和网关一样,否则会出现Destination host unreachable的错误(重点)
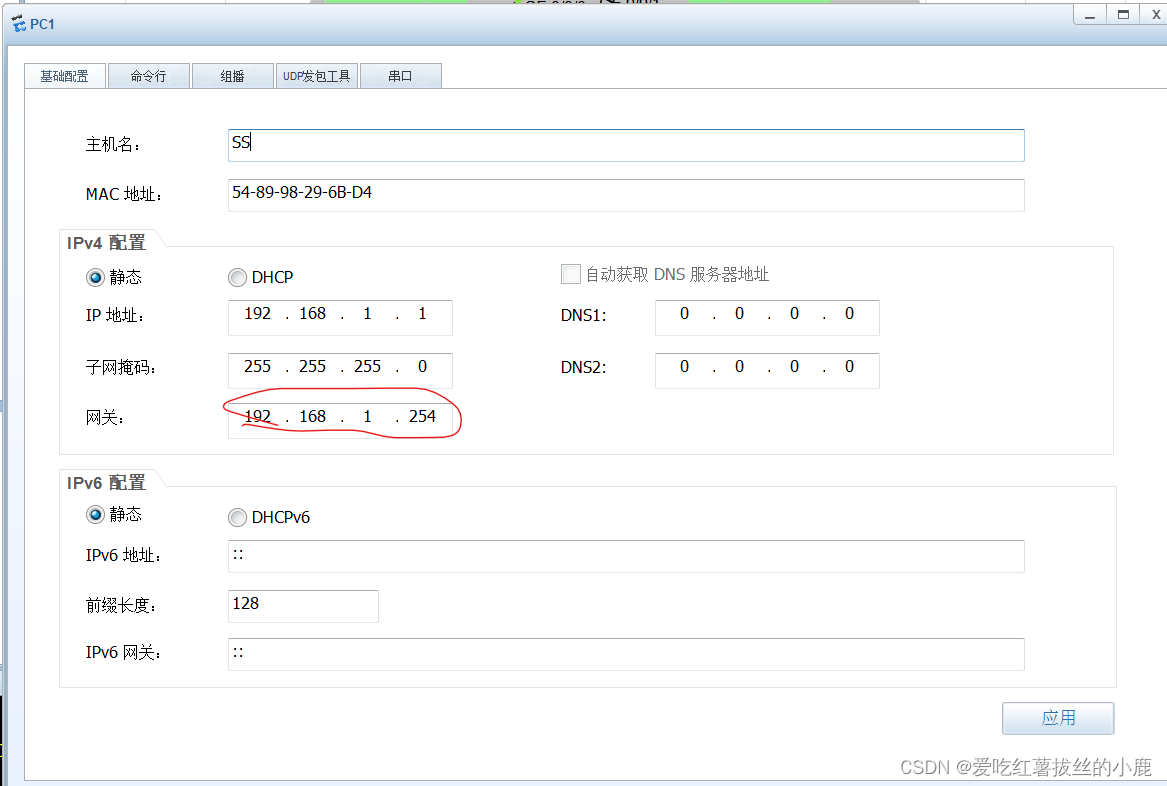
最后的效果
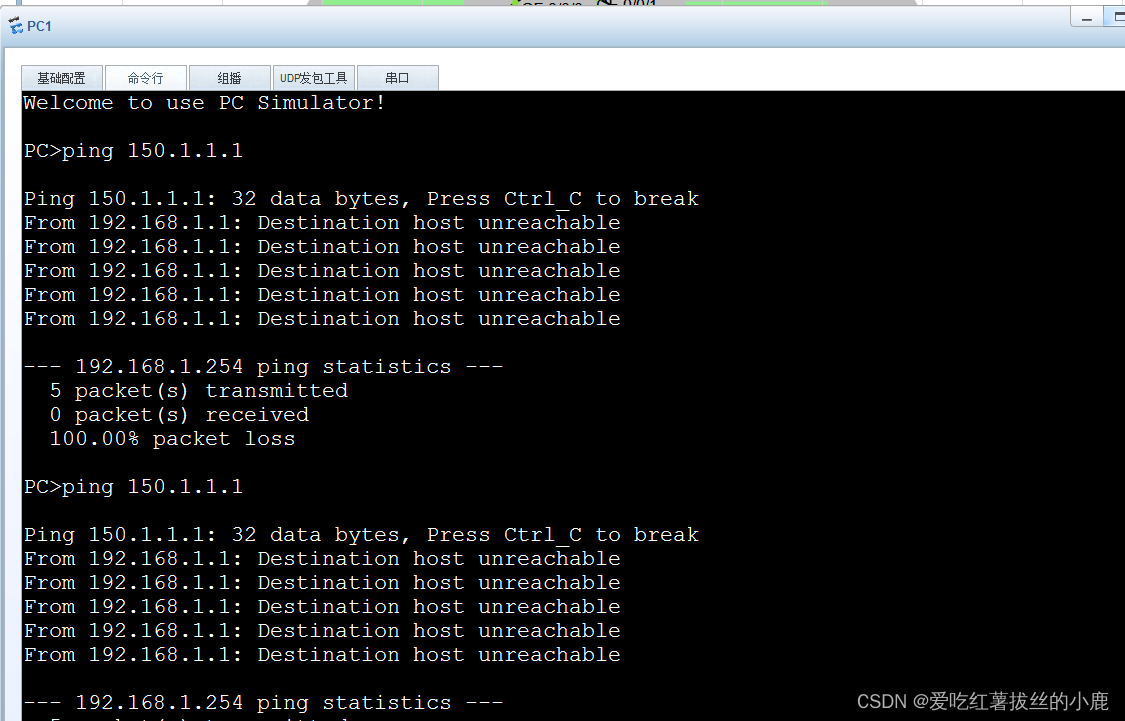
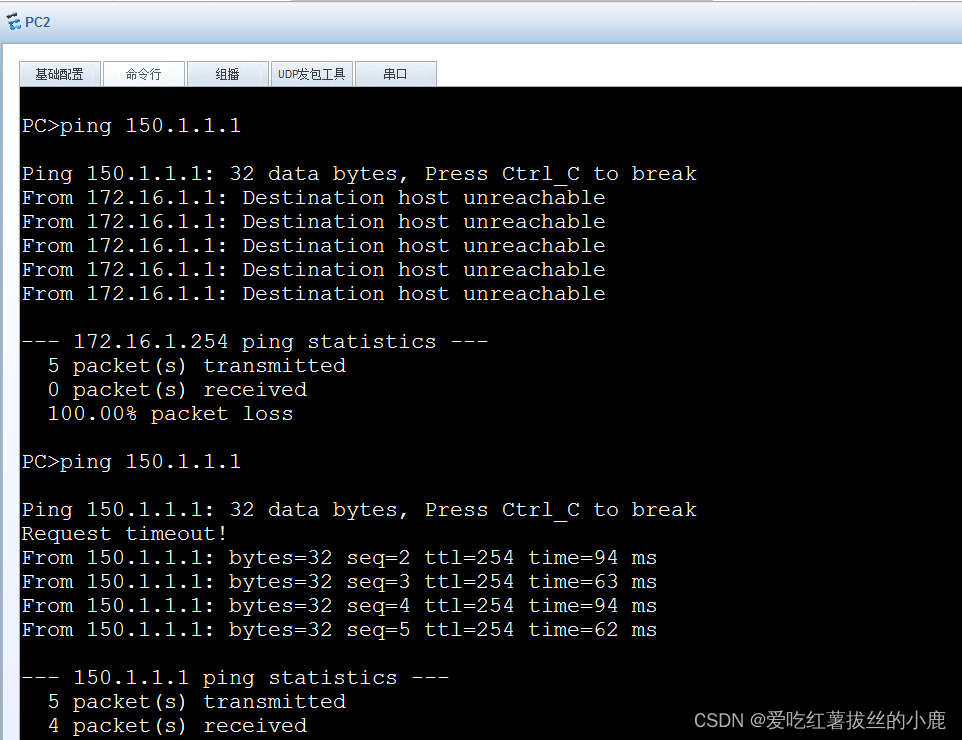
三.配置IPsec
R2配置
# 配置ACL:识别兴趣的流量
[AR2]acl 3001
[AR2-acl-adv-3001]rule permit ip source 192.168.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
[AR2-acl-adv-3001]di th
[V200R003C00]
#
acl number 3001
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
#
return
[AR2-acl-adv-3001]q
[AR2]
# 创建安全提议
[AR2]ipsec proposal ajest # 创建名为ajest 的安全提议
[AR2-ipsec-proposal-ajest]encapsulation-mode tunnel # 配置报文封装模式为隧道模式
[AR2-ipsec-proposal-ajest]transform esp # 配置隧道协议为ESP
[AR2-ipsec-proposal-ajest]esp authentication-algorithm sha1 # 配置认证算法为sha1
[AR2-ipsec-proposal-ajest]esp encryption-algorithm des # 配置加密算法为des
[AR2-ipsec-proposal-ajest]di th
[V200R003C00]
#
ipsec proposal ajest
esp authentication-algorithm sha1
#
return
[AR2-ipsec-proposal-ajest]q
[AR2]dis ipsec prop
Number of proposals: 1
IPSec proposal name: ajest
Encapsulation mode: Tunnel
Transform : esp-new
ESP protocol : Authentication SHA1-HMAC-96
Encryption DES
[AR2]
# 创建安全策略
[AR2]ipsec policy P1 10 manual # 进入手工配置模式
[AR2-ipsec-policy-manual-P1-10]security acl 3001 # 引用ACL
[AR2-ipsec-policy-manual-P1-10]proposal ajest # 引用安全提议
[AR2-ipsec-policy-manual-P1-10]tunnel local 100.1.1.2 # 本端地址
[AR2-ipsec-policy-manual-P1-10]tunnel remote 200.1.1.2 # 对端地址
[AR2-ipsec-policy-manual-P1-10]sa spi outbound esp 54321 # 出方向安全参数索引
[AR2-ipsec-policy-manual-P1-10]sa spi inbound esp 12345 # 入方向安全参数索引
[AR2-ipsec-policy-manual-P1-10]sa string-key outbound esp simple ajest
# 出方向认证密钥
[AR2-ipsec-policy-manual-P1-10]sa string-key inbound esp simple ajest
# 入方向认证密钥
[AR2-ipsec-policy-manual-P1-10]di th
[V200R003C00]
#
ipsec policy P1 10 manual
security acl 3001
proposal ajest
tunnel local 100.1.1.2
tunnel remote 200.1.1.2
sa spi inbound esp 12345
sa string-key inbound esp simple ajest
sa spi outbound esp 54321
sa string-key outbound esp simple ajest
#
return
[AR2-ipsec-policy-manual-P1-10]q
[AR2]
# 应用安全策略
[AR2]int g0/0/0
[AR2-GigabitEthernet0/0/0]ipsec policy P1
[AR2-GigabitEthernet0/0/0]di th
[V200R003C00]
#
interface GigabitEthernet0/0/0
ip address 100.1.1.2 255.255.255.0
ipsec policy P1
nat outbound 3000
#
return
[AR2-GigabitEthernet0/0/0]q
[AR2]
# 查看配置
[AR2]dis ipsec policy
===========================================
IPSec policy group: "P1"
Using interface: GigabitEthernet0/0/0
===========================================
Sequence number: 10
Security data flow: 3001
Tunnel local address: 100.1.1.2
Tunnel remote address: 200.1.1.2
Qos pre-classify: Disable
Proposal name:ajest
Inbound AH setting:
AH SPI:
AH string-key:
AH authentication hex key:
Inbound ESP setting:
ESP SPI: 12345 (0x3039)
ESP string-key: ajest
ESP encryption hex key:
ESP authentication hex key:
Outbound AH setting:
AH SPI:
AH string-key:
AH authentication hex key:
Outbound ESP setting:
ESP SPI: 54321 (0xd431)
ESP string-key: ajest
ESP encryption hex key:
ESP authentication hex key:
[AR2]
R3配置
[AR3]acl 3001
[AR3-acl-adv-3001]rule permit ip source 172.16.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
[AR3-acl-adv-3001]di th
[V200R003C00]
#
acl number 3001
rule 5 permit ip source 172.16.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
#
return
[AR3-acl-adv-3001]q
[AR3]
[AR3]ipsec proposal ajest
[AR3-ipsec-proposal-ajest]esp authentication-algorithm sha1
[AR3-ipsec-proposal-ajest]q
[AR3]di ipsec prop
Number of proposals: 1
IPSec proposal name: ajest
Encapsulation mode: Tunnel
Transform : esp-new
ESP protocol : Authentication SHA1-HMAC-96
Encryption DES
[AR3]
[AR3]ipsec policy P1 10 manual
[AR3-ipsec-policy-manual-P1-10]di th
[V200R003C00]
#
ipsec policy P1 10 manual
security acl 3001
proposal ajest
tunnel local 200.1.1.2
tunnel remote 100.1.1.2
sa spi inbound esp 54321
sa string-key inbound esp simple ajest
sa spi outbound esp 12345
sa string-key outbound esp simple ajest
#
return
[AR3-ipsec-policy-manual-P1-10]q
[AR3]
[AR3]int g0/0/0
[AR3-GigabitEthernet0/0/0]ipse
[AR3-GigabitEthernet0/0/0]ipsec po
[AR3-GigabitEthernet0/0/0]ipsec policy P1
[AR3-GigabitEthernet0/0/0]di th
[V200R003C00]
#
interface GigabitEthernet0/0/0
ip address 200.1.1.2 255.255.255.0
ipsec policy P1
nat outbound 3000
#
return
[AR3-GigabitEthernet0/0/0]q
[AR3]
在配置安全策略中安全参数索引也就是【 R2 】sa spi inbound esp 12345 sa spi outbound esp 54321,正好与【R3】sa spi inbound esp 54321,sa spi outbound esp 12345相互对应就像密码一样
四.NAT豁免
为什么要进行NAT豁免,当一个网关配置了防火墙 ,NAT ,IPsec VPN时,会先走NAT,也就是先走NAT的acl,而后走VPN的acl,所以NAT豁免的目的就是不走NAT的规则而走VPN的规则
[AR2]acl 3000
[AR2-acl-adv-3000]rule 4 deny ip source 192.168.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
[AR2-acl-adv-3000]di th
[V200R003C00]
#
acl number 3000
rule 4 deny ip source 192.168.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
rule 5 permit ip source 192.168.1.0 0.0.0.255
#
return
[AR2-acl-adv-3000]
[AR3]acl 3000
[AR3-acl-adv-3000]rule 4 deny ip source 172.16.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
[AR3-acl-adv-3000]di th
[V200R003C00]
#
acl number 3000
rule 4 deny ip source 172.16.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 5 permit ip source 172.16.1.0 0.0.0.255
#
return
[AR3-acl-adv-3000]
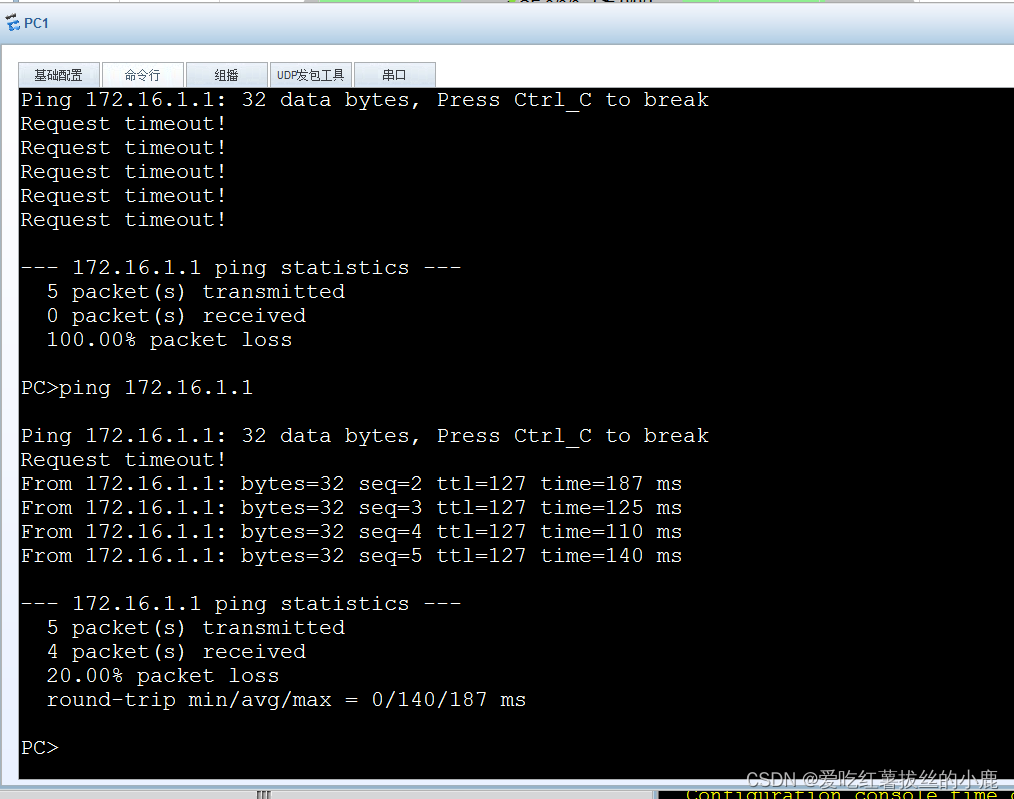
最后实现内网互通!!!!

 支付宝微信扫一扫,打赏作者吧~
支付宝微信扫一扫,打赏作者吧~本文链接:https://kinber.cn/post/4300.html 转载需授权!
推荐本站淘宝优惠价购买喜欢的宝贝:


