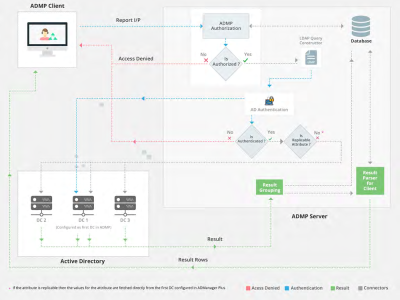
引言

自己部署一套免费的Radius,进行二次登录认证VMware Horizon和Citrix云桌面,无需集成第三方付费平台,完美运行。有需要的可以私信联系,文末可以自己获取教材。

环境准备
Rockey Linux 9.35 VMware Horizon 8
postgresql 14
VMware UAG 2406

文章目录
环境准备 Radius服务器配置
登录演示
UAG配置Radius
Radius对接域控
付费内容

Radius服务器配置
需要在rockey配置docker服务,已经配置完成,如图所示
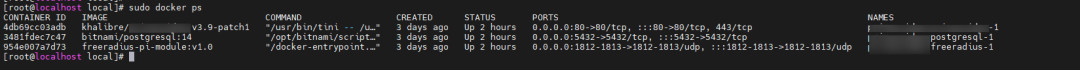
接着在docker里面安装freeradius组件。
freeradius docker 安装记录
docker安装freeradius
#拉取镜像docker pull freeradius/freeradius-server:latest#启动Freeradius容器docker run -d --name freeradius-server -p 1812-1813:1812-1813/udp freeradius/freeradius-server#查看容器是否正常启动docker ps -f name=freeradius-server#进入容器#docker exec -it freeradius sh#复制一份完整配置文件docker cp freeradius-server:/etc/freeradius ~/freeradius/config-bak#停止运行docker stop freeradius-server#保留需要的修改的配置文件,其余删除cd ~/freeradius/mkdir configcp ~/freeradius/config-bak/clients.conf config/clients.confcp ~/freeradius/config-bak/radiusd.conf config/radiusd.confcp ~/freeradius/config-bak/mods-available/eap config/eapcp ~/freeradius/config-bak/mods-config/files/authorize config/authorize #如果有自定义证书可以拷贝到config目录config/certs
进行配置修改
对config中的authorize、clients.conf、radiusd.conf、eap进行修改
authorize 对应 /etc/freeradius/mods-config/files/authorize
#添加下面一行用户配置,两个字符串分别是验证时输入的身份和密码"hzlarm" Cleartext-Password := "hzlarm123"
clients.conf 对应 /etc/freeradius/clients.conf
#配置客户端的密码以下是默认的,本机测试,配置这个点即可:client localhost secret = testing123#路由器添加radius服务器时需要 服务器ip与端口以及该secret,ipaddr是路由器的ip范围#设置为0.0.0.0/0任何ip都可以client private-network-1 { ipaddr = 0.0.0.0/0 secret = hzlarm123}radiusd.conf 对应 /etc/freeradius/radiusd.conf
#将所有(接受和拒绝)身份验证结果记录到日志文件中log {....auth = yes}eap 对应 /etc/freeradius/mods-available/eap
#eap的配置文件,默认tls,ttls,peap都包含,不需要的可以把相应的字段注释掉即可。eap { #eap未指定时,默认的类型。 default_eap_type = tls #default_eap_type = ttls #default_eap_type = peap #关联EAP请求数据包的列表,超时会被删除。 timer_expire = 60 #是否忽略不支持的eap请求。 ignore_unknown_eap_types = no # Cisco 用户名bug cisco_accounting_username_bug = no #限制服务器正在跟踪的会话数,有助于防止DoS攻击。此命令取自radiusdus.conf中的“max_requests”指令。 max_sessions = ${max_requests} tls-config tls-common { #private_key_password = whatever private_key_file = ${certdir}/srv.key certificate_file = ${certdir}/srv.crt ca_file = ${cadir}/ca.crt ca_path = ${cadir} tls_min_version = "1.0" tls_max_version = "1.2" # 如果网关客户端是TLS1.0要加这个否则失败 cipher_list = "DEFAULT@SECLEVEL=0" verify { #跳过额外检查 skip_if_ocsp_ok = yes #client = "/path/to/openssl verify -capath ${..ca_path} %{TLS-Client-Cert-Filename}" } } # Supported EAP-types ## EAP-TLS tls { tls = tls-common dh_file = ${certdir}/dh random_file = /dev/urandom #fragment_size = 1024 #include_length = yes #check_crl = yes #check_all_crl = yes #check_cert_issuer = "/C=GB/ST=Berkshire/L=Newbury/O=My Company Ltd" #check_cert_cn = %{User-Name} #virtual_server = check-eap-tls #使用freeradius -X调试时,默认使用该命令生成证书。 make_cert_command = "${certdir}/bootstrap" ecdh_curve = "prime256v1" cache { enable = no lifetime = 24 # hours max_entries = 255 } ocsp { enable = no override_cert_url = yes url = "http://127.0.0.1/ocsp/" } } peap { tls = tls-common default_eap_type = mschapv2 copy_request_to_tunnel = no use_tunneled_reply = no #proxy_tunneled_request_as_eap = yes virtual_server = "inner-tunnel" #soh = yes #soh_virtual_server = "soh-server" #require_client_cert = yes } ttls { tls = tls-common default_eap_type = md5 copy_request_to_tunnel = no use_tunneled_reply = no virtual_server = "inner-tunnel" #include_length = yes #require_client_cert = yes } mschapv2 { # send_error = no } md5 { } gtc{ }}
编辑 docker-compose 文件
# vi ~/freeradius/docker-compose.ymlversion: '3'services: freeradius: image: freeradius/freeradius-server container_name: freeradius ports: - 1812-1813:1812-1813/udp volumes: - ./logs:/var/log/freeradius - ./config/certs:/etc/freeradius/certs - ./config/clients.conf:/etc/freeradius/clients.conf - ./config/radiusd.conf:/etc/freeradius/radiusd.conf - ./config/eap:/etc/freeradius/mods-available/eap - ./config/authorize:/etc/freeradius/mods-config/files/authorize restart: always
启动
docker-compose up -d
docker-compose 命令
# 启动docker-compose up -d# 停止docker-compose stop#重启docker-compose restart
测试方法
安装测试工具eapol_test
Command line testing for EAP with FreeRADIUS
# Download and decompress wpa_supplicantwget https://w1.fi/releases/wpa_supplicant-2.9.tar.gztar -xzvf wpa_supplicant-2.9.tar.gz# Building eapol_testcd wpa_supplicant-2.9/wpa_supplicant/cp defconfig .configvi .config# Find the line containing #CONFIG_EAPOL_TEST=y and change it to CONFIG_EAPOL_TEST=ymake eapol_test#If an error occurs, execute this command#sudo apt-get install libdbus-1-dev libnl-3-dev libnl-genl-3-200 libnl-genl-3-dev libnl-idiag-3-devcp eapol_test /usr/local/bin/
eap-tls:
# sudo eapol_test -c eap-tls.conf -a 127.0.0.1 -p 1812 -s testing123 -r 1# 以下内容写在eap-tls.conf文件network={
eap=TLS eapol_flags=0
key_mgmt=IEEE8021X identity="hzlarm"
password="hzlarm123"
# self cert client
ca_cert="~/freeradius/config/certs/ca.crt"
client_cert="~/freeradius/config/certs/client.crt"
private_key="~/freeradius/config/certs/client.key"
private_key_passwd="whatever"
anonymous_identity="anonymous"}ttls-chap:
# sudo eapol_test -c ttls-chap.conf -a 127.0.0.1 -p 1812 -s testing123 -r 1# 以下内容写在ttls-chap.conf文件network={
ssid="example"
key_mgmt=WPA-EAP eap=TTLS identity="hzlarm"
anonymous_identity="anonymous"
password="hzlarm123"
phase2="auth=CHAP"#Uncomment the following to perform server certificate validation.# ca_cert="~/freeradius/config/certs/ca.crt"}ttls-eapmd5:
# sudo eapol_test -c ttls-eapmd5.conf -a 127.0.0.1 -p 1812 -s testing123 -r 1# 以下内容写在ttls-eapmd5.conf文件network={
ssid="example"
key_mgmt=WPA-EAP eap=TTLS identity="hzlarm"
anonymous_identity="anonymous"
password="hzlarm123"
phase2="autheap=MD5"#Uncomment the following to perform server certificate validation.# ca_cert="~/freeradius/config/certs/ca.crt"}ttls-mschapv2:
# sudo eapol_test -c ttls-mschapv2.conf -a 127.0.0.1 -p 1812 -s testing123 -r 1# 以下内容写在ttls-mschapv2.conf文件network={
ssid="example"
key_mgmt=WPA-EAP eap=TTLS identity="hzlarm"
anonymous_identity="anonymous"
password="hzlarm123"
phase2="autheap=MSCHAPV2"#Uncomment the following to perform server certificate validation.# ca_cert="~/freeradius/config/certs/ca.crt"}ttls-pap:
# sudo eapol_test -c ttls-pap.conf -a 127.0.0.1 -p 1812 -s testing123 -r 1# 以下内容写在ttls-pap.conf文件network={
ssid="example"
key_mgmt=WPA-EAP eap=TTLS identity="hzlarm"
anonymous_identity="anonymous"
password="hzlarm123"
phase2="auth=PAP"
#Uncomment the following to perform server certificate validation.# ca_cert="~/freeradius/config/certs/ca.crt"}
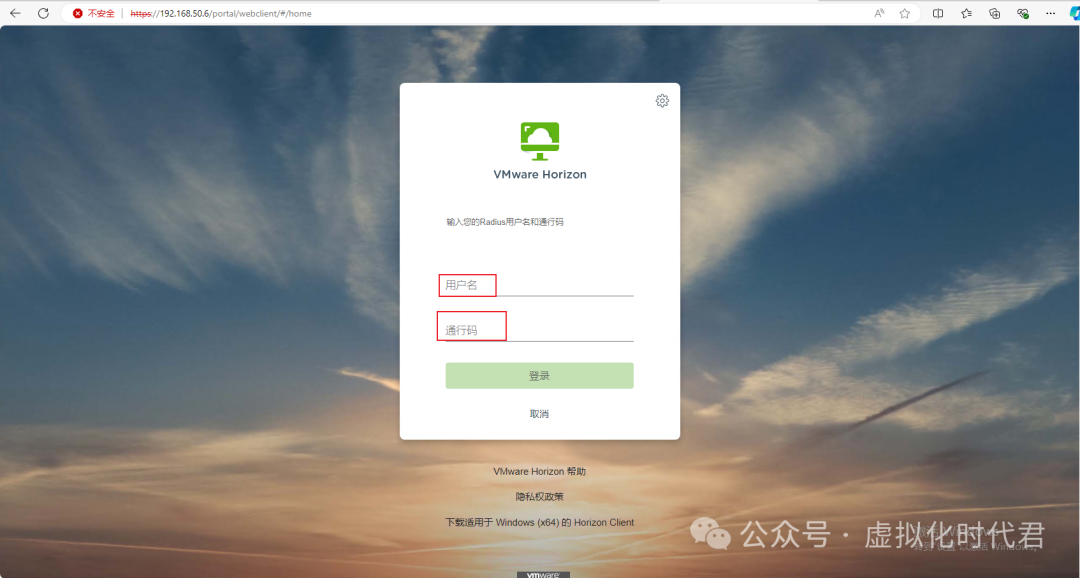
登录演示
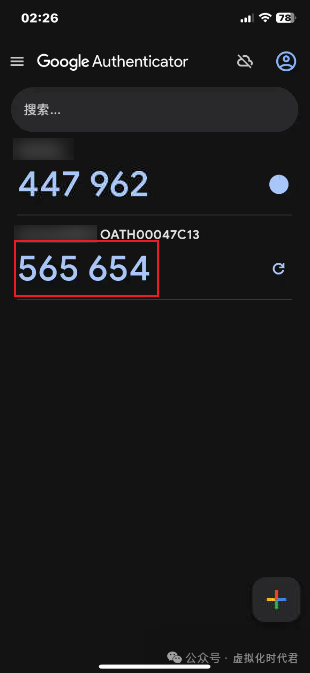
2.动态码口令
3.接着输入账号密码
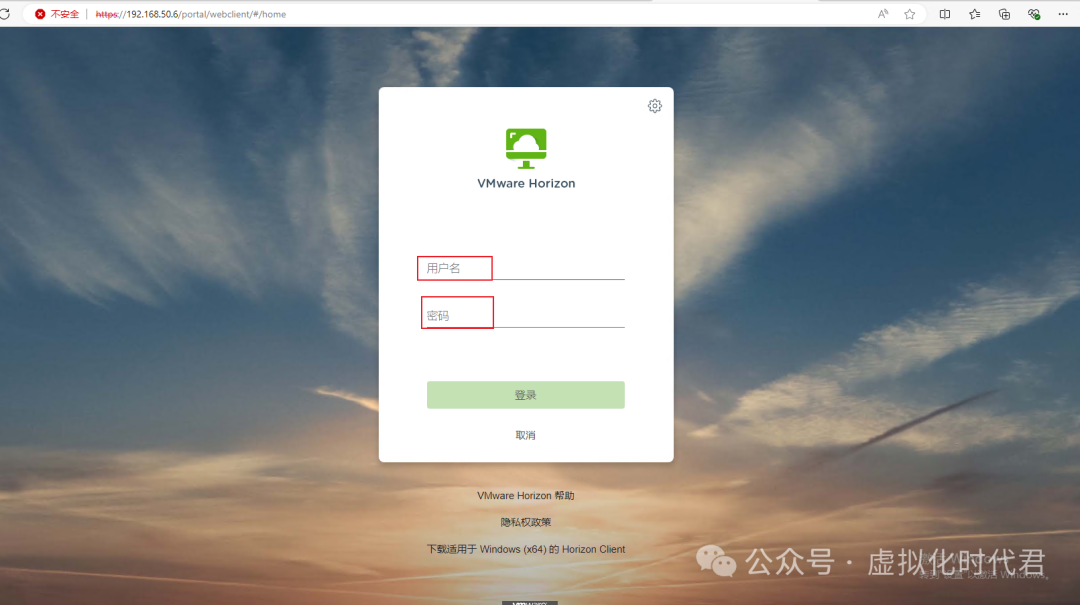
4.登录成功
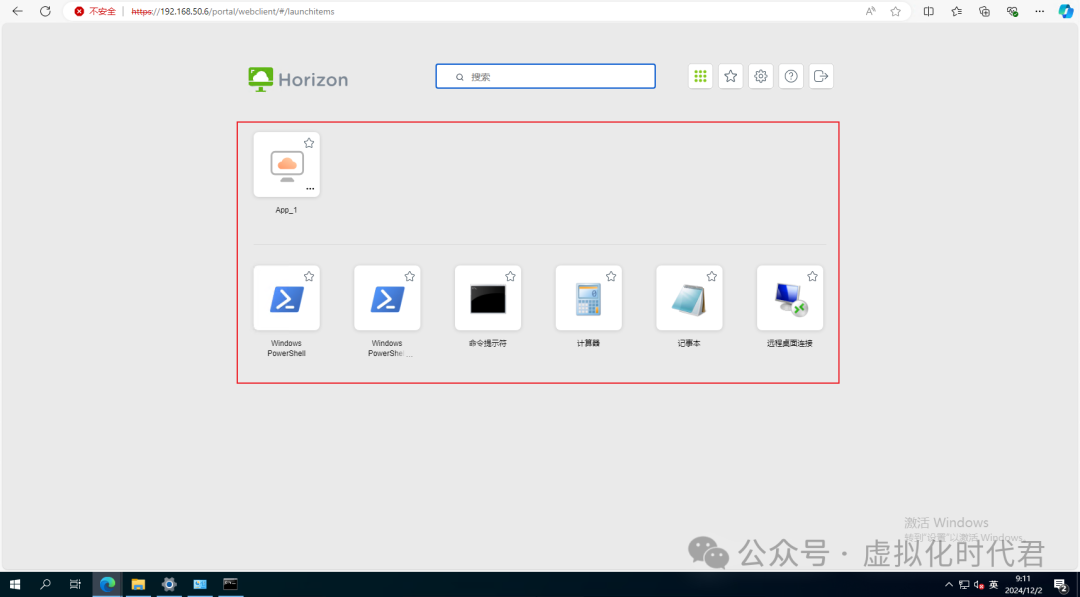
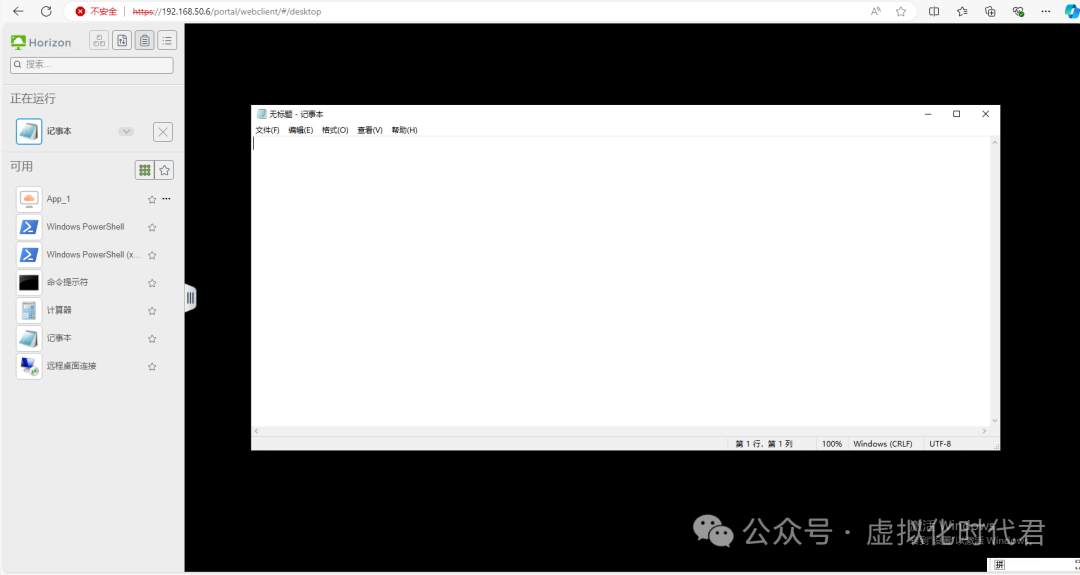
4.打开程序

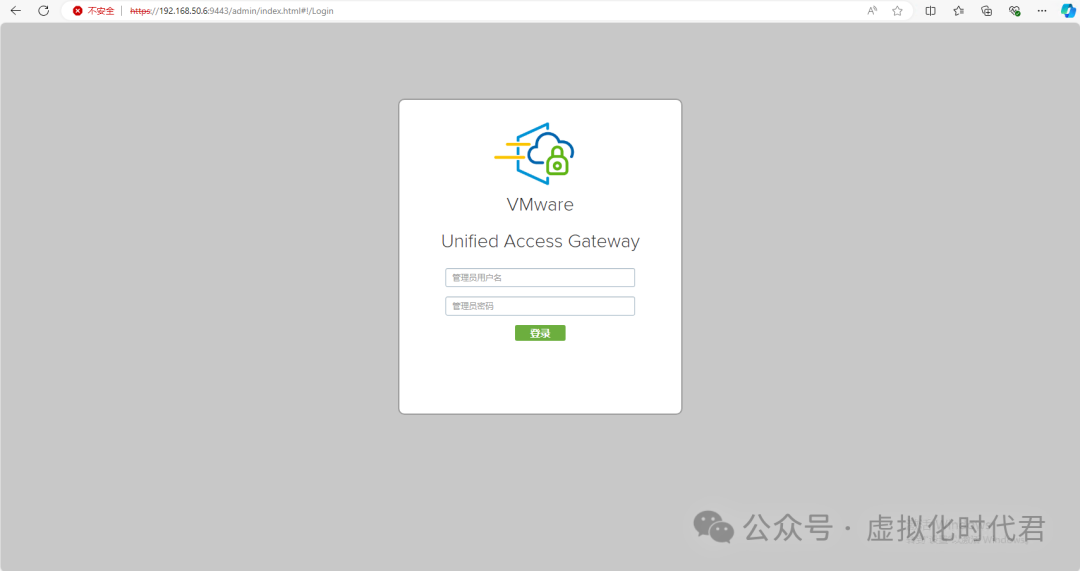
UAG配置教程
1.登录UAG网关
2.点击设置,开启radius
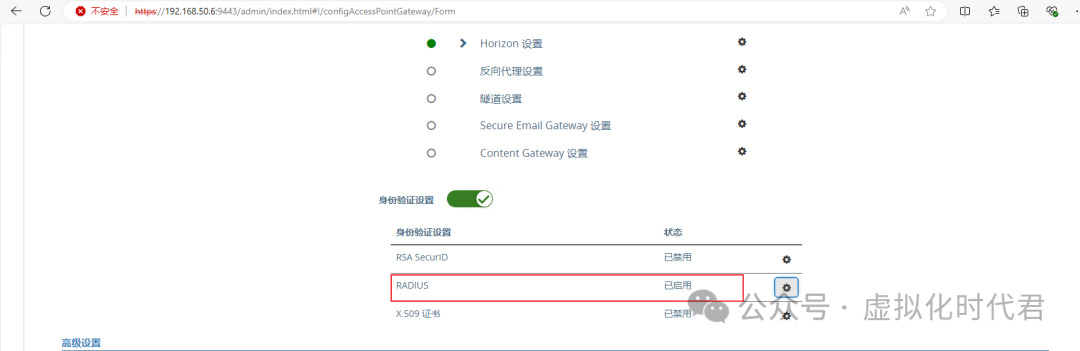
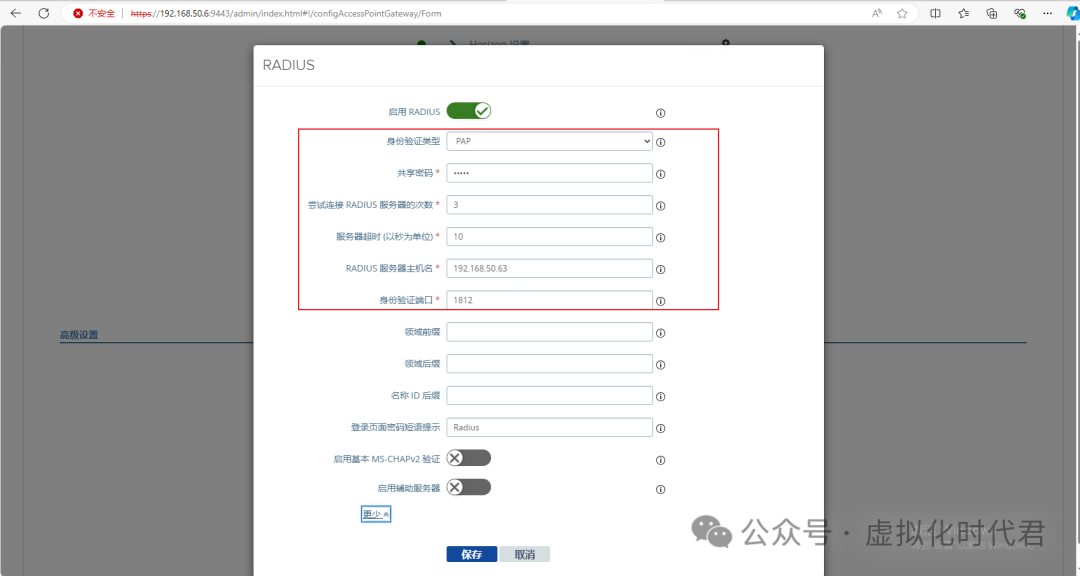
3.输入Radius的相关设置,端口一般为1812和1813
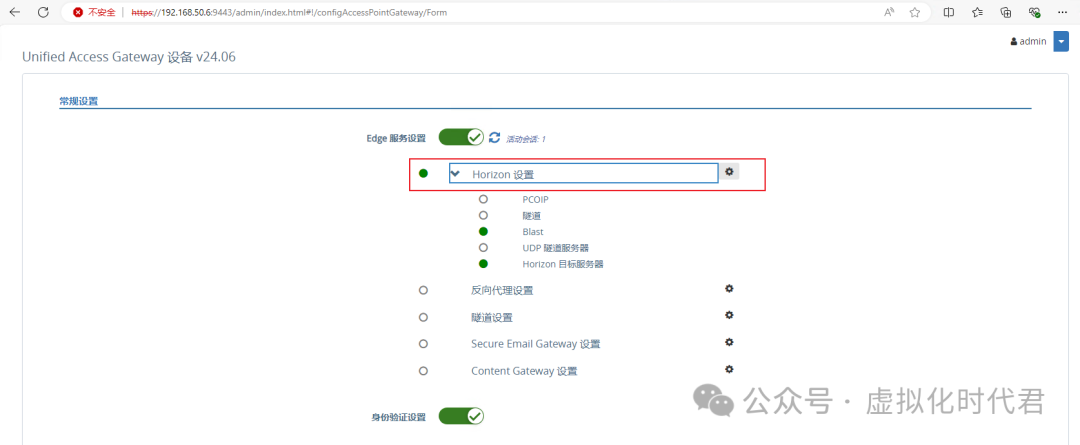
4.接着配置Horizon 的配置
5.其他配置不变,唯一变化是开启Radius的认证方法
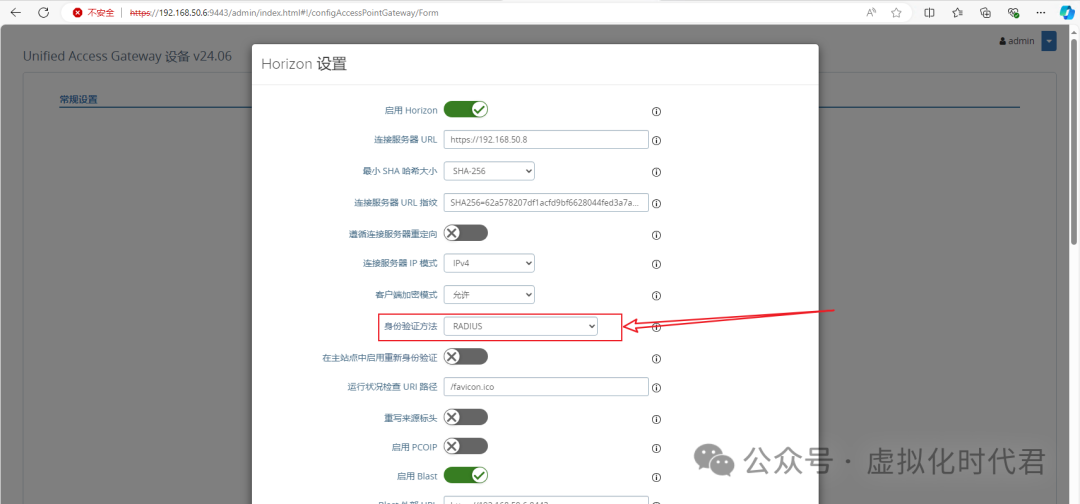
至此Radius配置完成。

Radius对接域控
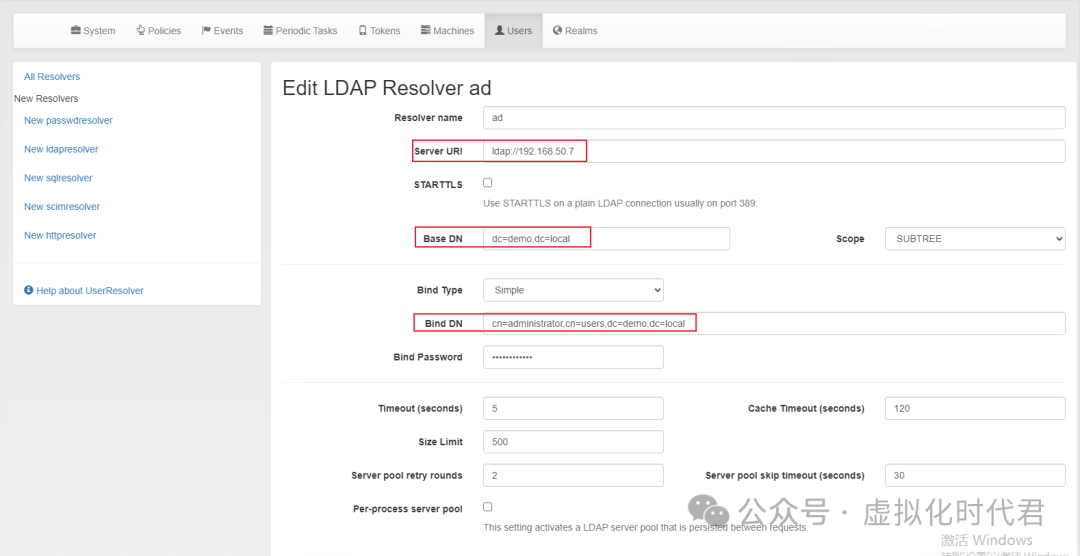
2.对接完同步我们的域账号
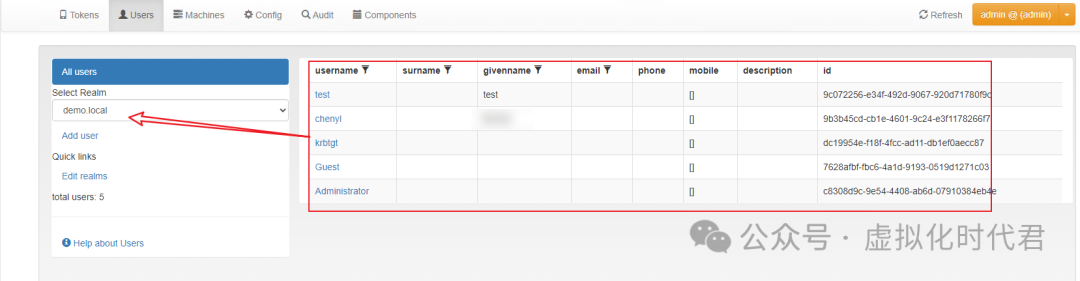
3.点击用户配置二次认证
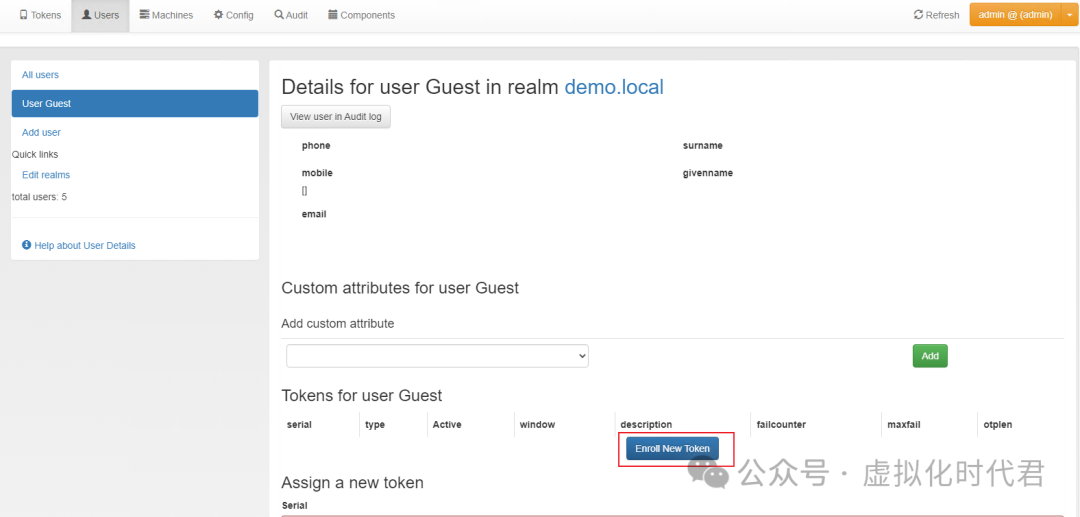
4.点击注册
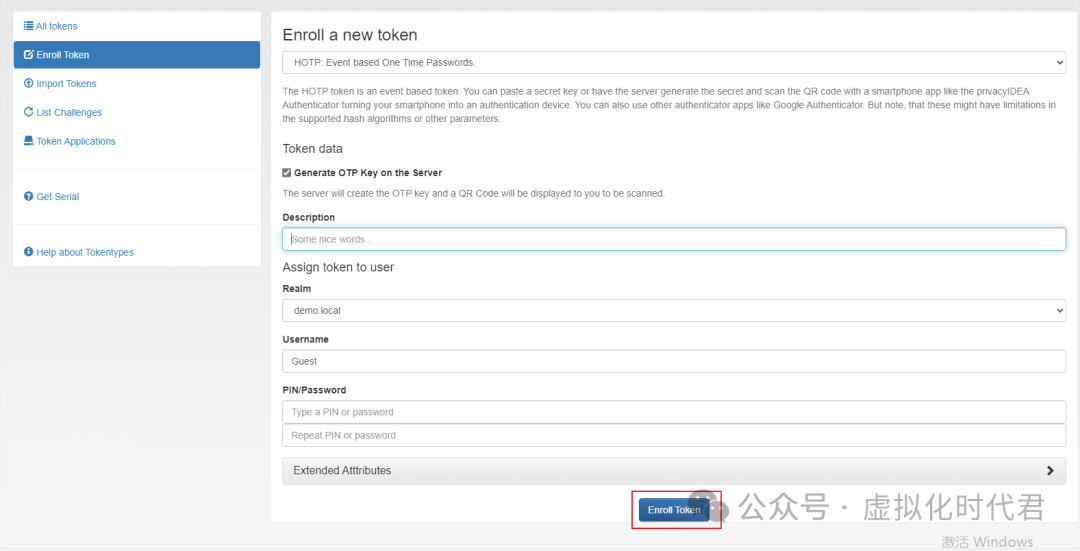
5.手机Google认证器扫描认证
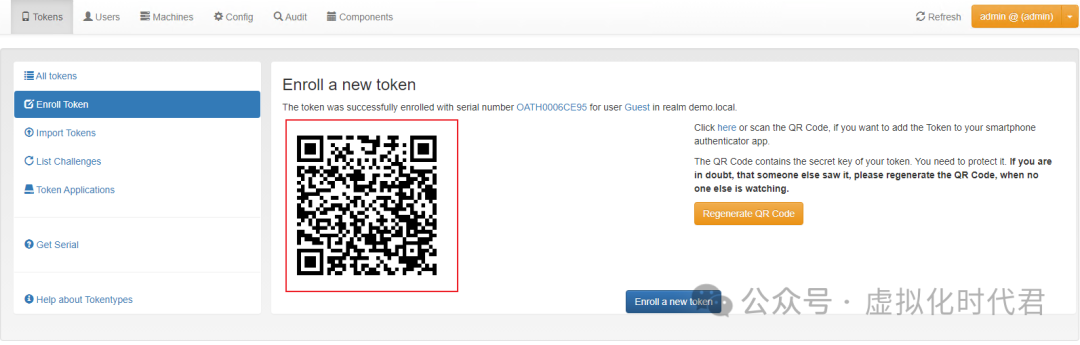
至此radius配置完成。

 支付宝微信扫一扫,打赏作者吧~
支付宝微信扫一扫,打赏作者吧~本文链接:https://kinber.cn/post/4065.html 转载需授权!
推荐本站淘宝优惠价购买喜欢的宝贝: