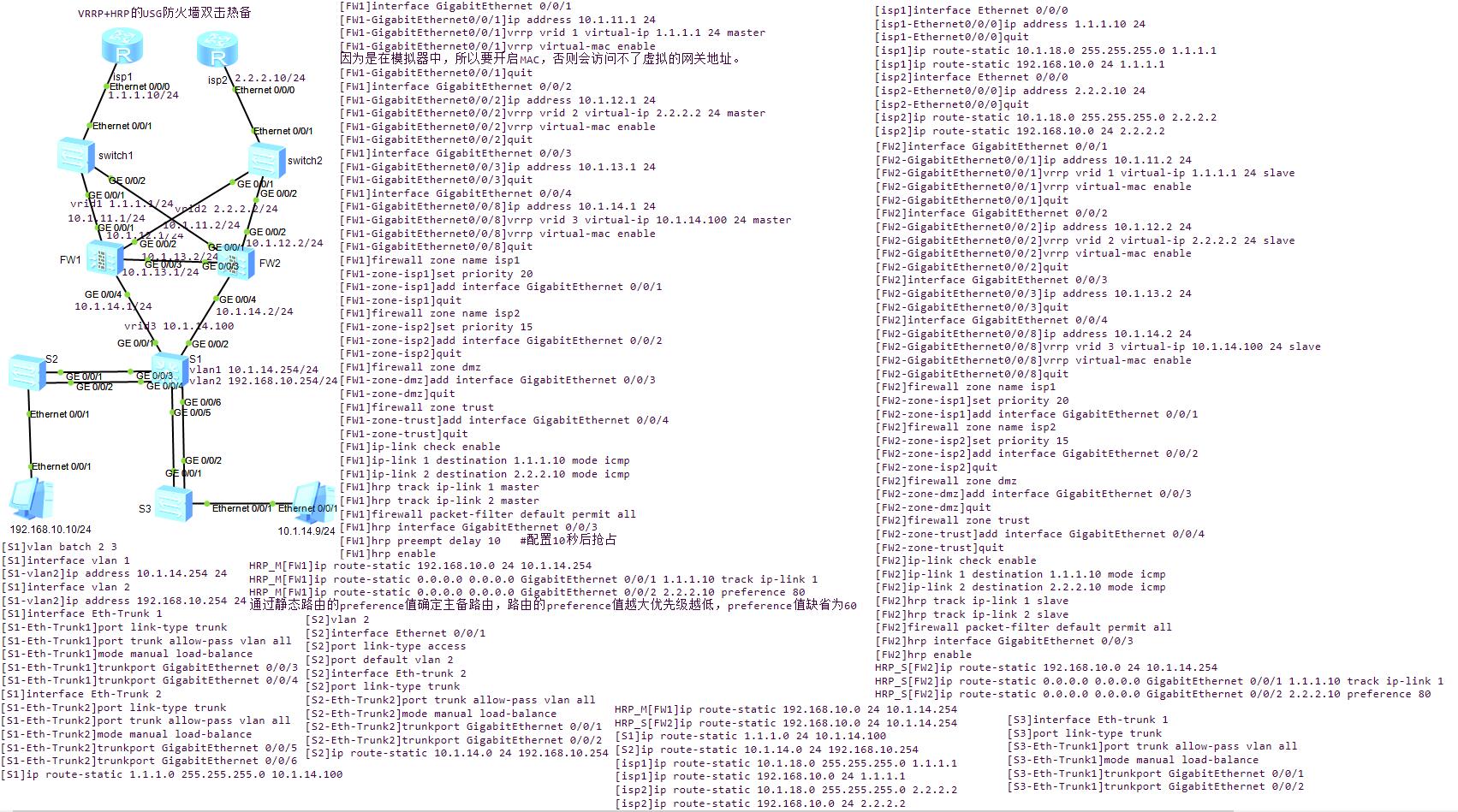
1.配置各接口IP以及vrrp,并加入相应的zone
(写vrid的时候一定要加入掩码比如/24,否则不允许不同网段的vrid存在)
2.给配置vrrp的接口下面启用vrrpvirtual-mac enable
这样vrid才可以ping到,尤其是在ensp中
3.isp1的vrrp为master,而isp2的vrrp为slave
4.暂时打开防火墙的所有通路
firewallpacket-filter default permit all
5.配置域间路由
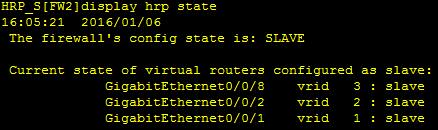
6.开启双击热备hrpenable
(如果已经开启了hrp又想在备墙上面做配置,可以通过开启配置来进行,
即:HRP_S[FW2]hrpslave config enable)
要添加的静态路由:
HRP_M[FW1]ip route-static 192.168.10.0 24 10.1.14.254
HRP_S[FW2]ip route-static 192.168.10.0 24 10.1.14.254
[S1]ip route-static 1.1.1.0 24 10.1.14.100
[S2]ip route-static 10.1.14.0 24 192.168.10.254
[isp1]ip route-static 10.1.18.0 255.255.255.0 1.1.1.1
[isp1]ip route-static 192.168.10.0 24 1.1.1.1
[isp2]ip route-static 10.1.18.0 255.255.255.0 2.2.2.2
[isp2]ip route-static 192.168.10.0 24 2.2.2.2
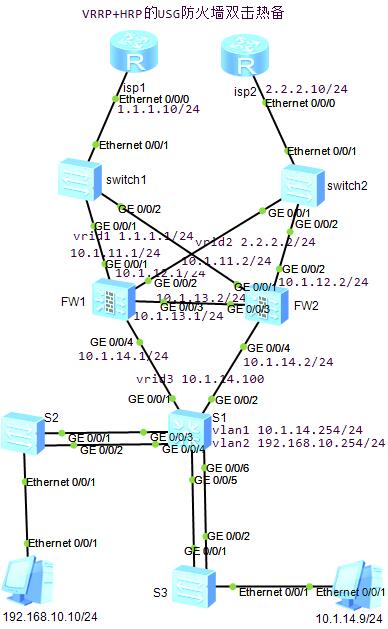
[FW1]interface GigabitEthernet 0/0/1
[FW1-GigabitEthernet0/0/1]ip address 10.1.11.1 24
[FW1-GigabitEthernet0/0/1]vrrp vrid 1 virtual-ip 1.1.1.1 24 master
[FW1-GigabitEthernet0/0/1]vrrp virtual-mac enable
因为是在模拟器中,所以要开启MAC,否则会访问不了虚拟的网关地址。
[FW1-GigabitEthernet0/0/1]quit
[FW1]interface GigabitEthernet 0/0/2
[FW1-GigabitEthernet0/0/2]ip address 10.1.12.1 24
[FW1-GigabitEthernet0/0/2]vrrp vrid 2 virtual-ip 2.2.2.2 24 master
[FW1-GigabitEthernet0/0/2]vrrp virtual-mac enable
[FW1-GigabitEthernet0/0/2]quit
[FW1]interface GigabitEthernet 0/0/3
[FW1-GigabitEthernet0/0/3]ip address 10.1.13.1 24
[FW1-GigabitEthernet0/0/3]quit
[FW1]interface GigabitEthernet 0/0/4
[FW1-GigabitEthernet0/0/8]ip address 10.1.14.1 24
[FW1-GigabitEthernet0/0/8]vrrp vrid 3 virtual-ip 10.1.14.100 24 master
[FW1-GigabitEthernet0/0/8]vrrp virtual-mac enable
[FW1-GigabitEthernet0/0/8]quit
[FW1]firewall zone name isp1
[FW1-zone-isp1]set priority 20
[FW1-zone-isp1]add interface GigabitEthernet 0/0/1
[FW1-zone-isp1]quit
[FW1]firewall zone name isp2
[FW1-zone-isp2]set priority 15
[FW1-zone-isp2]add interface GigabitEthernet 0/0/2
[FW1-zone-isp2]quit
[FW1]firewall zone dmz
[FW1-zone-dmz]add interface GigabitEthernet 0/0/3
[FW1-zone-dmz]quit
[FW1]firewall zone trust
[FW1-zone-trust]add interface GigabitEthernet 0/0/4
[FW1-zone-trust]quit
[FW1]ip-link check enable
[FW1]ip-link 1 destination 1.1.1.10 mode icmp
[FW1]ip-link 2 destination 2.2.2.10 mode icmp
[FW1]hrp track ip-link 1 master
[FW1]hrp track ip-link 2 master
[FW1]firewall packet-filter default permit all
[FW1]hrp interface GigabitEthernet 0/0/3
[FW1]hrp preempt delay 10 #配置10秒后抢占
[FW1]hrp enable
HRP_M[FW1]ip route-static 192.168.10.0 24 10.1.14.254
HRP_M[FW1]ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet 0/0/1 1.1.1.10 track ip-link 1
HRP_M[FW1]ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet 0/0/2 2.2.2.10 preference 80
通过静态路由的preference值确定主备路由,路由的preference值越大优先级越低,preference值缺省为60
[FW2]interface GigabitEthernet 0/0/1
[FW2-GigabitEthernet0/0/1]ip address 10.1.11.2 24
[FW2-GigabitEthernet0/0/1]vrrp vrid 1 virtual-ip 1.1.1.1 24 slave
[FW2-GigabitEthernet0/0/1]vrrp virtual-mac enable
[FW2-GigabitEthernet0/0/1]quit
[FW2]interface GigabitEthernet 0/0/2
[FW2-GigabitEthernet0/0/2]ip address 10.1.12.2 24
[FW2-GigabitEthernet0/0/2]vrrp vrid 2 virtual-ip 2.2.2.2 24 slave
[FW2-GigabitEthernet0/0/2]vrrp virtual-mac enable
[FW2-GigabitEthernet0/0/2]quit
[FW2]interface GigabitEthernet 0/0/3
[FW2-GigabitEthernet0/0/3]ip address 10.1.13.2 24
[FW2-GigabitEthernet0/0/3]quit
[FW2]interface GigabitEthernet 0/0/4
[FW2-GigabitEthernet0/0/8]ip address 10.1.14.2 24
[FW2-GigabitEthernet0/0/8]vrrp vrid 3 virtual-ip 10.1.14.100 24 slave
[FW2-GigabitEthernet0/0/8]vrrp virtual-mac enable
[FW2-GigabitEthernet0/0/8]quit
[FW2]firewall zone name isp1
[FW2-zone-isp1]set priority 20
[FW2-zone-isp1]add interface GigabitEthernet 0/0/1
[FW2]firewall zone name isp2
[FW2-zone-isp2]set priority 15
[FW2-zone-isp2]add interface GigabitEthernet 0/0/2
[FW2-zone-isp2]quit
[FW2]firewall zone dmz
[FW2-zone-dmz]add interface GigabitEthernet 0/0/3
[FW2-zone-dmz]quit
[FW2]firewall zone trust
[FW2-zone-trust]add interface GigabitEthernet 0/0/4
[FW2-zone-trust]quit
[FW2]ip-link check enable
[FW2]ip-link 1 destination 1.1.1.10 mode icmp
[FW2]ip-link 2 destination 2.2.2.10 mode icmp
[FW2]hrp track ip-link 1 slave
[FW2]hrp track ip-link 2 slave
[FW2]firewall packet-filter default permit all
[FW2]hrp interface GigabitEthernet 0/0/3
[FW2]hrp enable
HRP_S[FW2]ip route-static 192.168.10.0 24 10.1.14.254
HRP_S[FW2]ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet 0/0/1 1.1.1.10 track ip-link 1
HRP_S[FW2]ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet 0/0/2 2.2.2.10 preference 80
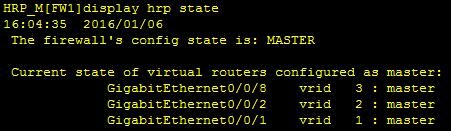
[isp1]interface Ethernet 0/0/0
[isp1-Ethernet0/0/0]ip address 1.1.1.10 24
[isp1-Ethernet0/0/0]quit
[isp1]ip route-static 10.1.18.0 255.255.255.0 1.1.1.1
[isp1]ip route-static 192.168.10.0 24 1.1.1.1
[isp2]interface Ethernet 0/0/0
[isp2-Ethernet0/0/0]ip address 2.2.2.10 24
[isp2-Ethernet0/0/0]quit
[isp2]ip route-static 10.1.18.0 255.255.255.0 2.2.2.2
[isp2]ip route-static 192.168.10.0 24 2.2.2.2
[S1]vlan batch 2 3
[S1]interface vlan 1
[S1-vlan2]ip address 10.1.14.254 24
[S1]interface vlan 2
[S1-vlan2]ip address 192.168.10.254 24
[S1]interface Eth-Trunk 1
[S1-Eth-Trunk1]port link-type trunk
[S1-Eth-Trunk1]port trunk allow-pass vlan all
[S1-Eth-Trunk1]mode manual load-balance
[S1-Eth-Trunk1]trunkport GigabitEthernet 0/0/3
[S1-Eth-Trunk1]trunkport GigabitEthernet 0/0/4
[S1]interface Eth-Trunk 2
[S1-Eth-Trunk2]port link-type trunk
[S1-Eth-Trunk2]port trunk allow-pass vlan all
[S1-Eth-Trunk2]mode manual load-balance
[S1-Eth-Trunk2]trunkport GigabitEthernet 0/0/5
[S1-Eth-Trunk2]trunkport GigabitEthernet 0/0/6
[S1]ip route-static 1.1.1.0 255.255.255.0 10.1.14.100
[S1]ip route-static 2.2.2.0 255.255.255.0 10.1.14.100
[S2]vlan 2
[S2]interface Ethernet 0/0/1
[S2]port link-type access
[S2]port default vlan 2
[S2]interface Eth-trunk 2
[S2]port link-type trunk
[S2-Eth-Trunk2]port trunk allow-pass vlan all
[S2-Eth-Trunk2]mode manual load-balance
[S2-Eth-Trunk2]trunkport GigabitEthernet 0/0/1
[S2-Eth-Trunk2]trunkport GigabitEthernet 0/0/2
[S2]ip route-static 10.1.14.0 24 192.168.10.254
[S3]interface Eth-trunk 1
[S3]port link-type trunk
[S3-Eth-Trunk1]port trunk allow-pass vlan all
[S3-Eth-Trunk1]mode manual load-balance
[S3-Eth-Trunk1]trunkport GigabitEthernet 0/0/1
[S3-Eth-Trunk1]trunkport GigabitEthernet 0/0/2
PC(192.168.10.10/24):
Pc的IP地址为192.168.10.10 255.255.255.0 192.168.10.254
网关一定要为三层vlan的IP地址来作为PC的网关。
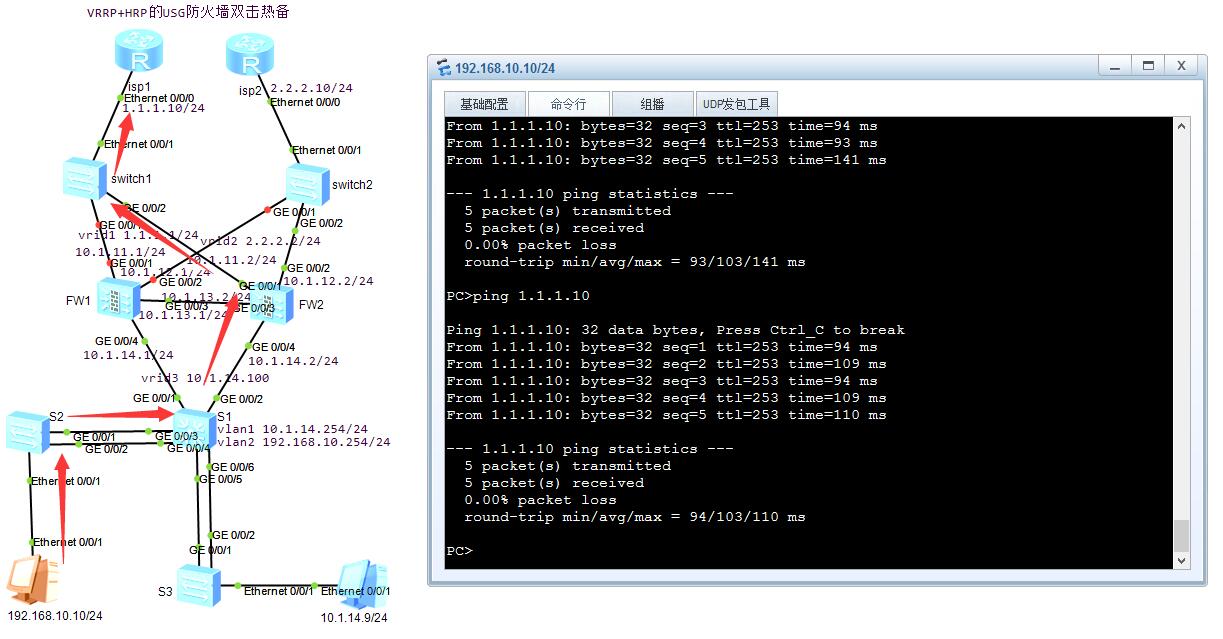
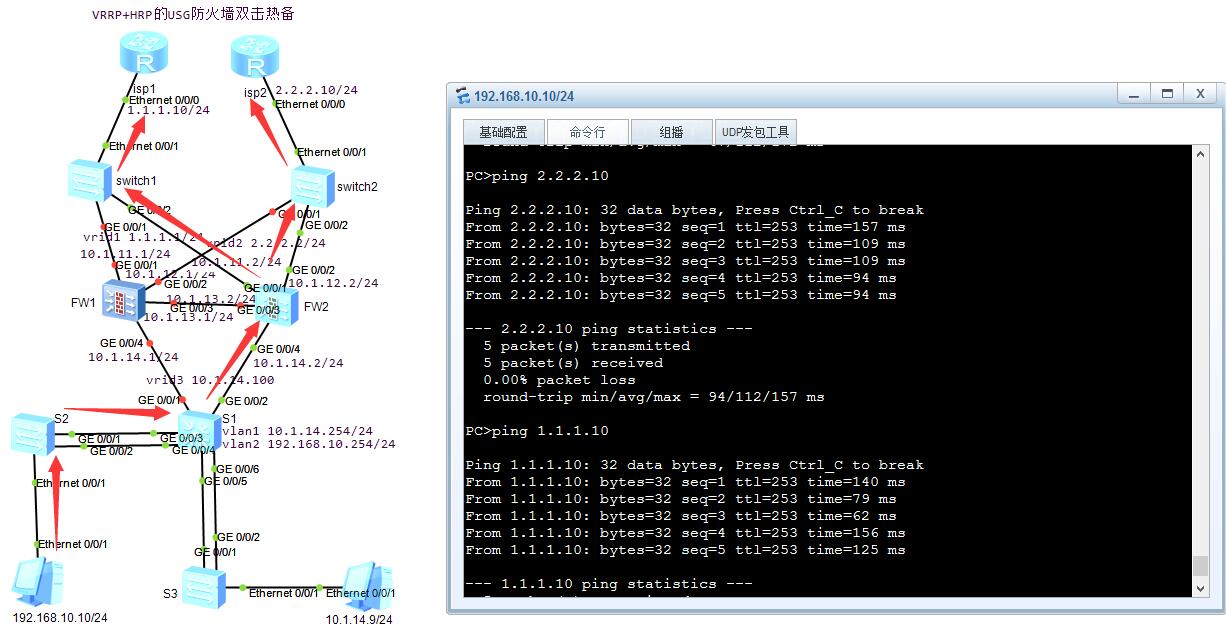
1.不使用3个公网地址也可以实现,不过得将两个物理口和虚拟出来的vrrp地址放在同一网段。
2.使ISP的一端用路由器代替即可,路由的wan口为公网地址,lan口为跟虚拟地址在同一网段的私网地址:
例如:
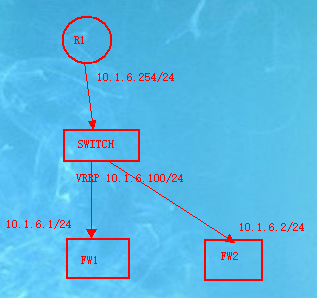
3.之所以要配置10.1.6.254和10.1.6.100的两个地址是因为R1下来的回程路由需要由10.1.6.100来作为网关,而10.1.6.254却是作为到公网的网关(如果直接将10.1.6.100的虚拟地址作为路由的lan口地址,则不能进行正常转发。)
————————————————
https://blog.csdn.net/u012402276/article/details/50484208
本文链接:https://kinber.cn/post/2670.html 转载需授权!
推荐本站淘宝优惠价购买喜欢的宝贝:

 支付宝微信扫一扫,打赏作者吧~
支付宝微信扫一扫,打赏作者吧~