先贴代码
今天来教大家怎么解密别人加密的js,为了方便调试,我们加密的例子很简单 console.log('magua');
var _0xodQ='jsjiami.com.v6',_0xodQ_=['_0xodQ'],_0x4dca=[_0xodQ,'wpnCm30=','jqZsrjATDtAiamil.fcom.vTD6Mp=='];if(function(_0x3e36fe,_0x55b35c,_0x385d02){function _0x2a493b(_0x5b0185,_0x2bff71,_0x2d62b1,_0x5dc4a4,_0x1c239e,_0x1ece41){_0x2bff71=_0x2bff71>>0x8,_0x1c239e='po';var _0x4f9849='shift',_0x25f1aa='push',_0x1ece41='';if(_0x2bff71<_0x5b0185){while(--_0x5b0185){_0x5dc4a4=_0x3e36fe[_0x4f9849]();if(_0x2bff71===_0x5b0185&&_0x1ece41===''&&_0x1ece41['length']===0x1){_0x2bff71=_0x5dc4a4,_0x2d62b1=_0x3e36fe[_0x1c239e+'p']();}else if(_0x2bff71&&_0x2d62b1['replace'](/[qZrATDtAlfTDMp=]/g,'')===_0x2bff71){_0x3e36fe[_0x25f1aa](_0x5dc4a4);}}_0x3e36fe[_0x25f1aa](_0x3e36fe[_0x4f9849]());}return 0x1013a8;};return _0x2a493b(++_0x55b35c,_0x385d02)>>_0x55b35c^_0x385d02;}(_0x4dca,0xff,0xff00),_0x4dca){_0xodQ_=_0x4dca['length']^0xff;};function _0x245f(_0x4ca09c,_0x166f45){_0x4ca09c=~~'0x'['concat'](_0x4ca09c['slice'](0x1));var _0x17ae61=_0x4dca[_0x4ca09c];if(_0x245f['uJjjRc']===undefined){(function(){var _0x5b7cb7=typeof window!=='undefined'?window:typeof process==='object'&&typeof require==='function'&&typeof global==='object'?global:this;var _0x15268a='ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=';_0x5b7cb7['atob']||(_0x5b7cb7['atob']=function(_0x486ab5){var _0x6b8ef3=String(_0x486ab5)['replace'](/=+$/,'');for(var _0x5c5f9d=0x0,_0x17c6c5,_0x563905,_0x5df67d=0x0,_0x47688d='';_0x563905=_0x6b8ef3['charAt'](_0x5df67d++);~_0x563905&&(_0x17c6c5=_0x5c5f9d%0x4?_0x17c6c5*0x40+_0x563905:_0x563905,_0x5c5f9d++%0x4)?_0x47688d+=String['fromCharCode'](0xff&_0x17c6c5>>(-0x2*_0x5c5f9d&0x6)):0x0){_0x563905=_0x15268a['indexOf'](_0x563905);}return _0x47688d;});}());function _0x34ec75(_0x5f1f12,_0x166f45){var _0x214a1f=[],_0x1fb9f9=0x0,_0x955dc,_0x1ff5d2='',_0x1f59d5='';_0x5f1f12=atob(_0x5f1f12);for(var _0x60941f=0x0,_0xf4689c=_0x5f1f12['length'];_0x60941f<_0xf4689c;_0x60941f++){_0x1f59d5+='%'+('00'+_0x5f1f12['charCodeAt'](_0x60941f)['toString'](0x10))['slice'](-0x2);}_0x5f1f12=decodeURIComponent(_0x1f59d5);for(var _0x4a70ae=0x0;_0x4a70ae<0x100;_0x4a70ae++){_0x214a1f[_0x4a70ae]=_0x4a70ae;}for(_0x4a70ae=0x0;_0x4a70ae<0x100;_0x4a70ae++){_0x1fb9f9=(_0x1fb9f9+_0x214a1f[_0x4a70ae]+_0x166f45['charCodeAt'](_0x4a70ae%_0x166f45['length']))%0x100;_0x955dc=_0x214a1f[_0x4a70ae];_0x214a1f[_0x4a70ae]=_0x214a1f[_0x1fb9f9];_0x214a1f[_0x1fb9f9]=_0x955dc;}_0x4a70ae=0x0;_0x1fb9f9=0x0;for(var _0x2d95ac=0x0;_0x2d95ac<_0x5f1f12['length'];_0x2d95ac++){_0x4a70ae=(_0x4a70ae+0x1)%0x100;_0x1fb9f9=(_0x1fb9f9+_0x214a1f[_0x4a70ae])%0x100;_0x955dc=_0x214a1f[_0x4a70ae];_0x214a1f[_0x4a70ae]=_0x214a1f[_0x1fb9f9];_0x214a1f[_0x1fb9f9]=_0x955dc;_0x1ff5d2+=String['fromCharCode'](_0x5f1f12['charCodeAt'](_0x2d95ac)^_0x214a1f[(_0x214a1f[_0x4a70ae]+_0x214a1f[_0x1fb9f9])%0x100]);}return _0x1ff5d2;}_0x245f['WbDzHT']=_0x34ec75;_0x245f['ZIlezY']={};_0x245f['uJjjRc']=!![];}var _0x3a092f=_0x245f['ZIlezY'][_0x4ca09c];if(_0x3a092f===undefined){if(_0x245f['ROPEwu']===undefined){_0x245f['ROPEwu']=!![];}_0x17ae61=_0x245f['WbDzHT'](_0x17ae61,_0x166f45);_0x245f['ZIlezY'][_0x4ca09c]=_0x17ae61;}else{_0x17ae61=_0x3a092f;}return _0x17ae61;};console[_0x245f('0',')*m#')]('magua');;_0xodQ='jsjiami.com.v6';
格式化一下,看看代码结构
var _0xodR = 'jsjiami.com.v6', _0xodR_ = ['_0xodR'],
_0x2190 = [_0xodR, 'wrbDvsKBwo4L', 'DAdo', 'jsjwiamHDFYi.cuYZlwom.CXvf6ge=='];
if (function (_0x2495fa, _0x3bf006, _0x100650) {
function _0x3b33c5(_0x54dff1, _0x164ebe, _0x32273e, _0x285dfc, _0x17a2c3, _0x7c092c) {
_0x164ebe = _0x164ebe >> 0x8, _0x17a2c3 = 'po';
var _0x550248 = 'shift', _0x56e977 = 'push', _0x7c092c = '';
if (_0x164ebe < _0x54dff1) {
while (--_0x54dff1) {
_0x285dfc = _0x2495fa[_0x550248]();
if (_0x164ebe === _0x54dff1 && _0x7c092c === '' && _0x7c092c['length'] === 0x1) {
_0x164ebe = _0x285dfc, _0x32273e = _0x2495fa[_0x17a2c3 + 'p']();
} else if (_0x164ebe && _0x32273e['replace'](/[wHDFYuYZlwCXfge=]/g, '') === _0x164ebe) {
_0x2495fa[_0x56e977](_0x285dfc);
}
}
_0x2495fa[_0x56e977](_0x2495fa[_0x550248]());
}
return 0x1013a4;
}
return _0x3b33c5(++_0x3bf006, _0x100650) >> _0x3bf006 ^ _0x100650;
}(_0x2190, 0x1c3, 0x1c300), _0x2190) {
_0xodR_ = _0x2190['length'] ^ 0x1c3;
}
function _0x2e58(_0xb479be, _0x4bb6ab) {
_0xb479be = ~~'0x'['concat'](_0xb479be['slice'](0x1));
var _0x1ce7ab = _0x2190[_0xb479be];
if (_0x2e58['ZnyOlV'] === undefined) {
(function () {
var _0x28d2fd = typeof window !== 'undefined' ? window : typeof process === 'object' && typeof require === 'function' && typeof global === 'object' ? global : this;
var _0x5c3961 = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=';
_0x28d2fd['atob'] || (_0x28d2fd['atob'] = function (_0x363646) {
var _0x3b7cce = String(_0x363646)['replace'](/=+$/, '');
for (var _0x13baec = 0x0, _0x5e5845, _0x3c5167, _0x31fd7a = 0x0, _0x4462fe = ''; _0x3c5167 = _0x3b7cce['charAt'](_0x31fd7a++); ~_0x3c5167 && (_0x5e5845 = _0x13baec % 0x4 ? _0x5e5845 * 0x40 + _0x3c5167 : _0x3c5167, _0x13baec++ % 0x4) ? _0x4462fe += String['fromCharCode'](0xff & _0x5e5845 >> (-0x2 * _0x13baec & 0x6)) : 0x0) {
_0x3c5167 = _0x5c3961['indexOf'](_0x3c5167);
}
return _0x4462fe;
});
}());
function _0x175702(_0x3b5cdb, _0x4bb6ab) {
var _0x5012ac = [], _0x5cc4d8 = 0x0, _0x11c3a0, _0x36393a = '', _0x48a116 = '';
_0x3b5cdb = atob(_0x3b5cdb);
for (var _0x7d3665 = 0x0, _0x5ce8fb = _0x3b5cdb['length']; _0x7d3665 < _0x5ce8fb; _0x7d3665++) {
_0x48a116 += '%' + ('00' + _0x3b5cdb['charCodeAt'](_0x7d3665)['toString'](0x10))['slice'](-0x2);
}
_0x3b5cdb = decodeURIComponent(_0x48a116);
for (var _0x496c04 = 0x0; _0x496c04 < 0x100; _0x496c04++) {
_0x5012ac[_0x496c04] = _0x496c04;
}
for (_0x496c04 = 0x0; _0x496c04 < 0x100; _0x496c04++) {
_0x5cc4d8 = (_0x5cc4d8 + _0x5012ac[_0x496c04] + _0x4bb6ab['charCodeAt'](_0x496c04 % _0x4bb6ab['length'])) % 0x100;
_0x11c3a0 = _0x5012ac[_0x496c04];
_0x5012ac[_0x496c04] = _0x5012ac[_0x5cc4d8];
_0x5012ac[_0x5cc4d8] = _0x11c3a0;
}
_0x496c04 = 0x0;
_0x5cc4d8 = 0x0;
for (var _0x1833e3 = 0x0; _0x1833e3 < _0x3b5cdb['length']; _0x1833e3++) {
_0x496c04 = (_0x496c04 + 0x1) % 0x100;
_0x5cc4d8 = (_0x5cc4d8 + _0x5012ac[_0x496c04]) % 0x100;
_0x11c3a0 = _0x5012ac[_0x496c04];
_0x5012ac[_0x496c04] = _0x5012ac[_0x5cc4d8];
_0x5012ac[_0x5cc4d8] = _0x11c3a0;
_0x36393a += String['fromCharCode'](_0x3b5cdb['charCodeAt'](_0x1833e3) ^ _0x5012ac[(_0x5012ac[_0x496c04] + _0x5012ac[_0x5cc4d8]) % 0x100]);
}
return _0x36393a;
}
_0x2e58['ijKboh'] = _0x175702;
_0x2e58['VAzepW'] = {};
_0x2e58['ZnyOlV'] = !![];
}
var _0x2d1a4a = _0x2e58['VAzepW'][_0xb479be];
if (_0x2d1a4a === undefined) {
if (_0x2e58['ZMLlec'] === undefined) {
_0x2e58['ZMLlec'] = !![];
}
_0x1ce7ab = _0x2e58['ijKboh'](_0x1ce7ab, _0x4bb6ab);
_0x2e58['VAzepW'][_0xb479be] = _0x1ce7ab;
} else {
_0x1ce7ab = _0x2d1a4a;
}
return _0x1ce7ab;
}console[_0x2e58('0', 't1KB')](_0x2e58('1', '0Yl$'));
_0xodR = 'jsjiami.com.v6';
js解密一定要有良好的心理素质,看到一堆代码不要慌,我们慢慢分析,先把第一个代码块拎出来分析,看上去这些变量名就是经过了js编码和解码处理
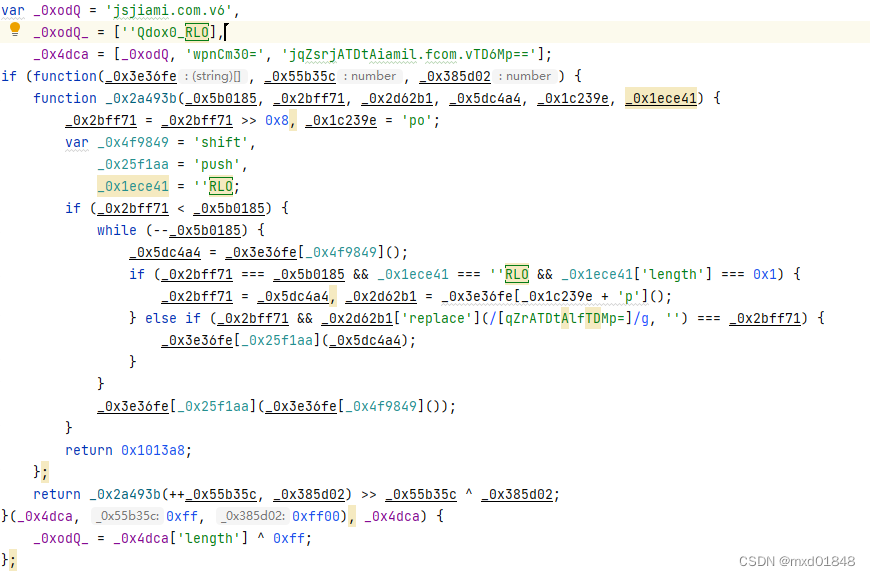
_0x4dca是一个字符串数组,有几个元素看上去是Base64编码后的样子。我试了下,解出来都是乱码。
然后下边一大串代码,仔细看的话其实整个函数返回的是一个布尔类型的值作为if的判断条件。
我们把这个函数单独拎出来,代码就变成下边这样了。
const v = function(_0x3e36fe, _0x55b35c, _0x385d02) {
function _0x2a493b(_0x5b0185, _0x2bff71, _0x2d62b1, _0x5dc4a4, _0x1c239e, _0x1ece41) {
_0x2bff71 = _0x2bff71 >> 0x8, _0x1c239e = 'po';
var _0x4f9849 = 'shift',
_0x25f1aa = 'push',
_0x1ece41 = '';
if (_0x2bff71 < _0x5b0185) {
while (--_0x5b0185) {
_0x5dc4a4 = _0x3e36fe[_0x4f9849]();
if (_0x2bff71 === _0x5b0185 && _0x1ece41 === '' && _0x1ece41['length'] === 0x1) {
_0x2bff71 = _0x5dc4a4, _0x2d62b1 = _0x3e36fe[_0x1c239e + 'p']();
} else if (_0x2bff71 && _0x2d62b1['replace'](/[qZrATDtAlfTDMp=]/g, '') === _0x2bff71) {
_0x3e36fe[_0x25f1aa](_0x5dc4a4);
}
}
_0x3e36fe[_0x25f1aa](_0x3e36fe[_0x4f9849]());
}
return 0x1013a8;
};
return _0x2a493b(++_0x55b35c, _0x385d02) >> _0x55b35c ^ _0x385d02;
}(_0x4dca, 0xff, 0xff00);
if (v, _0x4dca) {
_0xodQ_ = _0x4dca['length'] ^ 0xff;
}
我们先看整体结构有什么变化,函数和if分离了,if中有2个值,逗号分割了,这时候是否执行函数内的代码块由最后一个参数决定,也就是_0x4dca。而上边代码中_0x4dca是一个数组,那么if就永远为true,if里的代码也就是永远都执行的了。我们先看下这串代码做了什么
_0x4dca = ['jsjiami.com.v6', 'wpnCm30=', 'jqZsrjATDtAiamil.fcom.vTD6Mp=='];
_0xodQ_ = _0x4dca['length'] ^ 0xff;
// 也就是
_0xodQ_ = 3 ^ 255 = 252;
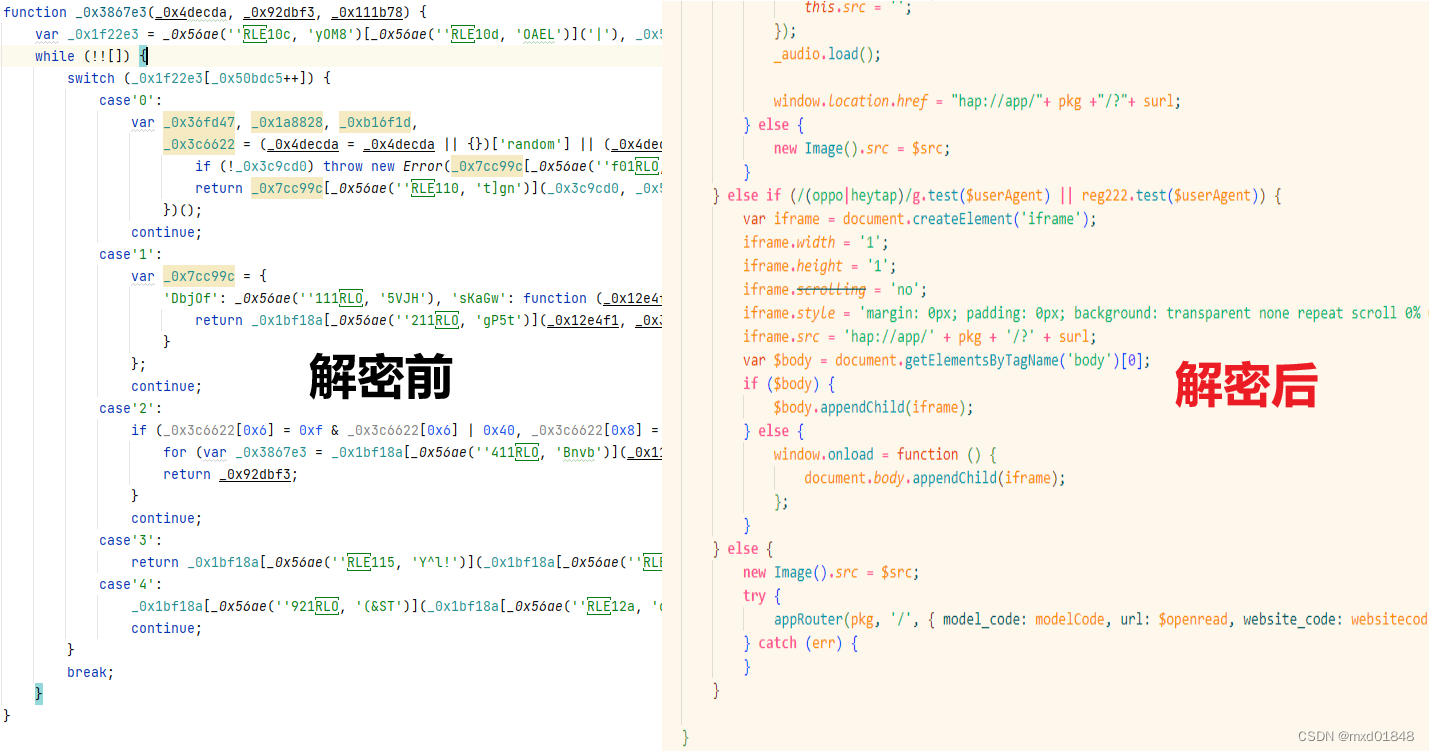
上边的函数体也同理,都可以用这个方法一步步解出来,看看这个方法的作用是什么。这是最简单也是最慢的解密方式。
整体解密思路如下
1.先格式化
2.看整体代码结构
3.将大的加密代码剖析成一个个小的代码块
4.挨个解密一个个小的代码块,明白每个小代码块的业务目的
5.把所有解密的结果汇总做总结
----------分享一个好用的js代码解密工具--------
一般的加密能直接解出来,难一点的加密解完后比之前阅读好很多,难一点的加密可以先在线解密再自己人工解密。
www.jsjiami.com https://www.jsjiami.com/jiemi.html
JS解密-JS在线解密-JS脚本解密-JS格式化去注释-JS美化 - [JavaScript加密]
本文链接:https://kinber.cn/post/3157.html 转载需授权!
推荐本站淘宝优惠价购买喜欢的宝贝:

 支付宝微信扫一扫,打赏作者吧~
支付宝微信扫一扫,打赏作者吧~